| Sections of this page | |
| (1) Out of Box Experience | (2) Wi-Fi Features |
| (3) Upgrading The Firmware | (4) Poking Around the UI |
| (5) External and Internal Access Ports | (6) Guest Wi-Fi Network |
| (7) VPN Client | (8) LAN Side Nmap Again |
| (9) Spying On The Router | (10) Living with the router |
| (11) Out of The Box Defaults | (12) Interesting Features |
| (13) Making Mesh | (14) Hidden WiFi Network |
| (15) Synology Resources | (16) Updates to this page |
This page is mostly but not exclusively focused on security. It is my experience, observations and thoughts using Synology's second generation router, the RT2600ac. I started using the router in September 2019 and most of the tire kicking was done with firmware version 1.2.3-8017 Update 2 from August 2019.
RT2600ac OUT OF BOX EXPERIENCE
First thing I noticed is that, as routers go, it's fairly big. And, its ugly.
There is an on/off in the back which, in my opinion, is a bad thing. For one, it's not needed; routers are intended to run all the time. If you ever need to turn it off you can just unplug the power cable. In fact, the power cable is right next to the on/off switch. More importantly, the switch can break. It's a spring type switch that you push in and out. I had a switch just like this fail on an Asus router. Nothing could keep the button pushed in. Had to throw the router out.
There are buttons on the side of the router for WPS, Wi-Fi and Eject. The buttons are black in the middle of a black case, so hard to see. Worse, the letters describing the button are also black, so pretty much impossible to read without a flashlight. On the other hand, having a Wi-Fi on/off button is a good security feature because it makes it very easy to turn off Wi-Fi when it's not needed.
The Ethernet ports on the back are plastic rather than metal, a surprisingly cheap way to go on a relatively expensive router. Instead of LEDs on the Ethernet ports themselves, it has an LED indicator for each Ethernet port on the top of the router. Green indicates a gigabit connection, orange indicates a connection speed of either 10 or 100 Mbps.
The default router and Wi-Fi passwords are on a label on the bottom. Many routers do this.
FIRST TIME SETUP
The Quick Install Guide setup booklet covers the barest minimum you need to do to get started. Its all pictures no words. There are 9 LED lights on the front of the router and the booklet does not explain what they indicate. After you turn on a router, you have to wait a bit until it has fully booted. The Guide says nothing about this and nothing about how you can tell when it has finished booting. FYI: when the status light changes from orange to green, it has finished booting. Screw things up? It says nothing about how to reset back to factory defaults.
It also doesn't say that you are better off downloading and reading the 29-page Hardware Installation Guide. That said, the Hardware Install Guide is not well done. For example, it says "If you wish to use Smart WAN, connect your RT2600ac (at the WAN1 and LAN1 ports) to the ISP modem with network cables" What is Smart WAN? Doesn't say. It is an advanced feature and does not belong at the very beginning of the Hardware Install guide. And, no ISP modem has two Ethernet ports. To use Smart WAN you need two modems. From what I have seen, all the documentation for this router was written by people who do not understand the technology.
Like every other router I have seen, the setup instructions say nothing about running the initial setup while the router is off-line. Fortunately, this is possible with the RT2600ac. Also like every other router, it assumes you have a modem from your ISP rather than addressing the messy option of a combination modem/router.
The Hardware Installation Guide says the default Wi-Fi SSID is "Synology_(Serial)". The label on the bottom of the router, says the default SSID is "SynologyRouter".
I ran the initial setup from a Chromebook that was connected to the router via Wi-Fi.
Right off the bat, I didn't like it. The router creates a captive portal which took control of the Chromebook to the point that I could not run any other apps. All I could was the initial router walk-through. I was truly captive. Being captive, I could not read the EULA or the Privacy Statement. Not only did the setup routine cover them up, I also could not scroll either document.
The initial setup requires you to chose both a userid and a password to logon to the router with. I think its great when a router lets you change the userid, many only let you pick a password. It accepted a short six character password without objection.
The initial setup asks about external access to SRM. It does not say what SRM is and many people will not know. It is the Synology router operating system, what other routers call their firmware. The pros and cons are not explained. At least you can change this later.
My router shipped with SRM version 1.1.7-6941 Update 3 which originally shipped in August 2018.
The default subnet is 192.168.1.x with the router at 192.168.1.1. You can also get to the web interface of the router with http://router.synology.com.
INITIAL WIFI
The initial setup creates one SSID that lives on both Wi-Fi frequency bands and uses WPA2 Personal encryption. Par for the course.
On the 2.4GHz frequency band it chose channel 8, a really bad choice. The router lives in a very crowded Wi-Fi neighborhood making it all the more important that it stick with the three non-overlapping channels: 1, 6 and 11. Channel 8 benefits no one, devices on channels 6 and 8 interfere with each other much more than they would if they were all on the same channel. It is a lose-lose situation. After cold booting, it again chose channel 8. At least it used the standard channel width of 20MHz. Some routers hog multiple channels by using a 40MHz wide channel on the 2.4GHz band.
On the 5GHz band it used a channel width of 80MHz. This is good for performance when there are no neighbors, however, in a crowded environment, it is better to use a narrower channel. There is no one right answer. It would be better to ask during setup if there are many wireless networks in the area and adjust the channel width accordingly. As with every other router I have seen, there is no discussion of how often the channel is re-evaluated.
FIRST ROUTER LOGONS
The first time you logon to web interface of the router, there is a short intro wizard that explains a bit about the user interface. It stinks. The biggest omission is that it does not explain how to log out of the router. I knew how thanks to my experience with their NAS boxes. It is not intuitive. In contrast, every Peplink web page has a logoff button in roughly the same place.
After this intro, you are prompted to create an account with Synology at account.synology.com. But why? What features are enabled by having an account? I am very hesitant to create an account because of the potential for spying. Peplink, Amplifi and Asus allow you to use their routers without having an account. It is getting to be a rare feature.
You are also offered a chance to modify the self-update settings, which is good. The bad part is that the options are confusing (they are the same as on their NAS devices). Simply put, one option always gets the latest software, the other option only installs updates to the current version of SRM. You can have it auto-update or not, which is great. Auto-updating is off by default, a strange choice. If it does auto-update, you can tell it when to do (think Sunday at 2AM). I have not seen a router handle software updates any better than Synology. Even the routers that auto-update can't hold a candle to Synology. They even provide a link the release notes for the software you are about to install.
When I later tried to logon to the web interface using router.synology.com from an Android device, I could not. Rather than be prompted for the userid/password, it told me to Launch DS Router, the Synology app for their routers. I then tried accessing the router using 192.168.1.1 but the result was the same. Switching to another web browser changed nothing. Humbug. When I switched to a Windows PC, I was able to use the web interface.
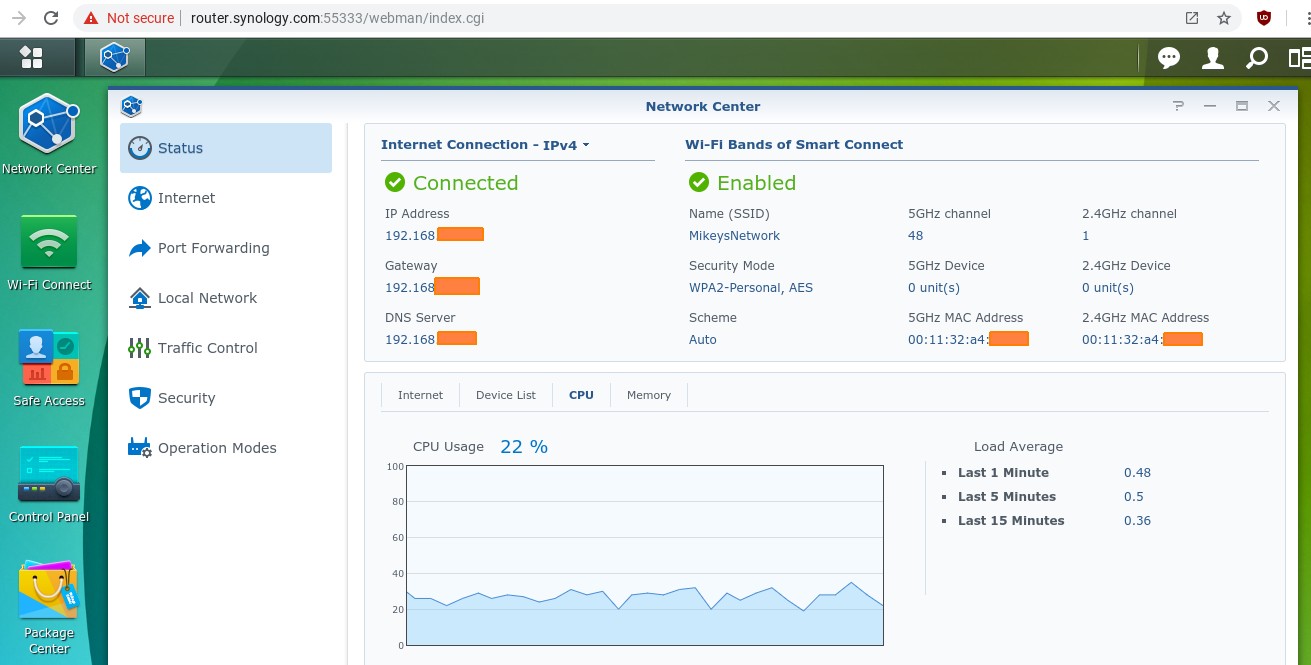
While poking around the main status display (at Network Center -> Status and shown above), I found that CPU usage hovered around 20% which is concerning. At the time, the router was not connected to the Internet and only one device was connected to it, a laptop computer via Ethernet. I let it sit a bit but the CPU usage graph remained around 20%. It also reports a "Load Average" percentage that drastically disagrees with the CPU usage graph. After more than 20 minutes, the Load Averages were 3.4 (last minute), 3.4 (last 5 minutes) and 2.7 (last 15 minutes). Again, the graph showed CPU usage around 20% the whole time. This pattern continued even after upgrading the firmware. In the screen shot above, you see the graph shows CPU usage just above 20% while the Load Average for the last minute is under 1 percent.
You will also note in the screen shot above of the main Status display that it displays an IP Address, a Gateway IP address and a DNS server IP address. Every router has two IP addresses, an internal one (LAN) and an external one (WAN). The display should say which one it is showing. Better yet, it should display both. This router actually has three IP addresses since the Guest network is on a different subnet than the main/private network. When the Guest network is being used, the router should display all three IP addresses. But, no.
The list of connected devices was also disappointing. If you want to keep an eye on this, you will also want to assign devices a name that means something to you, such as Harvey's iPad. It does not let you assign your own names to devices that use the router - here. I later learned that you can do this at Network Center -> Traffic Control. Not very intuitive.
IP version 6 (IPv6) defaults to Auto, which means it may be enabled, or, it may not, depending on the mode of the server from the WAN port (their words, not mine). You can disable IPv6 at Network Center -> Internet -> Connection tab. Personally, I have no use for IPv6, its just another potential hole in whatever VPN I am using.
On the upside, the router has context-sensitive help built into the web interface. Each window has a question mark icon in the top right corner that brings up the Help page for that window. Great.
The router supports Wake On LAN.
WI-FI FEATURES top
It supports WPA2 Enterprise which offers better security than WPA2 Personal. In fact, Synology offers the best support of WPA2 Enterprise that I am aware of - they let you run a RADIUS server right on the router. This was perhaps the main reason I purchased the router in the first place. For more on WPA2 Enterprise see the WPA2 WPA3 WiFi Encryption page.
It supports WEP which offers very poor security and hardly any new routers still support it. Given a choice between serving a mass market of consumers by lowering security or focusing on security, Synology shows where they stand with choices like this, still supporting WEP many years after it was disgraced for poor security. They have the same choice when it comes to WPS and again, the router enables WPS by default out of the box. Clearly the router is targeted at consumers.
Speaking of WPS, it supports three flavors: AP PIN code, client PIN code, and Push Button. You can disable WPS entirely, but not each flavor individually. That's too bad as the Push Button mode might be useful. The AP PIN code mode is the dangerous one. To disable WPS: Network center -> Wireless -> WPS tab.
Two other indicators show where Synology stands on security: UPnP and Ping reply. If you care about security, you disable these by default.
UPnP was enabled by default. Of course it was. Every consumer router enables UPnP. Doing so cuts down on tech support requests. It also makes you much less secure as it lets devices on your network poke holes in the router firewall. UPnP is controlled at Network Center -> Local Network -> General tab.
Needless to say, I disabled UPnP. It didn't like that. The Network Center app hung. Other apps ran fine, but the Network Center was frozen. I could not even X out of it, so I had no choice but to re-boot the router. Ugh.
As for Ping reply, I could not find any option in the web interface to control the Ping reply behavior. It my testing, it replied to Pings on the LAN side from the private network, but not on the WAN side and not on the LAN side from a Guest Wi-Fi network.
The RT2600ac supports a mixed mode of WPA and WPA2 encryption for backward compatibility. This mixed mode is labeled as "High" security, which I disagree with. Nothing using WPA can be considered high security. It also supports MAC address filtering as do most routers.
CONFIGURING WI-FI
I was confused by the user interface for configuring Wi-Fi in firmware version 1.1.7. Fortunately, it has changed in newer firmware. Part of my confusion stemmed from Synology inventing new terminology ("Smart Connect", "wireless mode" and "scheme") and has an option that I had never seen before. As for Smart Connect, with it off, you get to configure each Wi-Fi frequency band individually. With it on, many configuration options disappear. Specifically:
With Smart Connect on:
- There is an option called "Scheme" that is set to Auto. You can change the scheme to Custom to configure band steering options. That's for later.
- There is a wireless mode option that can only be set to Auto. Mode? Could mean many things.
- The channel with and Channel number can only be set to Auto
- The transmit power can be set to High, Middle or Low.
- An option called "PMF Support" can be Disabled, Optional or Required. PMF? WTF? According to Synology it is "Required to provide your device with the ability to modify internal settings to address configuration conditions." I have no clue.
- There is an AP isolation option and I suspect the description is wrong. It can "prevent communication between devices connected to the same Wi-Fi band of your Synology router." Taken a face value, this makes no sense at all. Hundreds of devices connect to both Wi-Fi frequency bands. Why create a feature if you can't explain what it does to your customers? This is also a drastic contrast to Peplink where the meaning of their isolation options are crystal clear.
- You can set a schedule for Wi-Fi to be On or Off. This seems to apply to all Wi-Fi, not to individual SSIDs.
With Smart Connect Off:
- There are now have two SSIDs instead of one. Each frequency band has its own SSID, just like the bad old days. Yuck.
- You can chose two wireless modes in the 5ghz band: a and n and ac -or- just ac. In the 2.4GHz band you can chose either b and g and n -or- just n. So, thats what it means.
- You can chose your preferred channel and channel width for each frequency band
- Each frequency band can be scheduled independently
- You can chose the transmit power for each frequency band
So ... you can have total control over the Wi-Fi settings, but the cost is having to live with different SSIDs on each frequency band. Again, this has changed with newer firmware.
NMAP PORT SCANNING
From an Ethernet connected Windows PC, I ran nmap against the LAN side of the router. I has more holes than swiss cheese. Just looking at TCP (no UDP) these ports were open: 53, 80, 161, 443, 515, 5440, 7787, 8000 and 8001. 80 is used by HTTP to access web pages, 443 is used by HTTPS for secure web pages. Port 161 is SNMP and is particularly troubling because the SNMP service is disabled. You see this at Control Panel -> Services. If the service is not running, the port should be closed. And, if the service is not running, who or what replied to the nmap probe? Makes no sense.
Both ports 53 and 5440 were running dnsmasq version 2.78-49-g2265dec according to nmap. Dnsmasq provides both DNS and DHCP servers. The latest version is 2.80 (released Oct. 2018), version 2.78 was released October 2017.
Nmap could not recognize the software running on port 7787. Both ports 8000 and 8001 were detected as the Apache web server. They are the default ports for HTTP and HTTPS. Port 515 is only identified as printer. Before trying to close these ports, it's time to upgrade to the latest firmware.
Updating the SRM firmware
UPGRADING TO THE LATEST FIRMWARE top
September 13, 2019: I upgraded the firmware (SRM) to version 1.2.3-8017 from July 24, 2019. The download hung at 88% for a long time, but eventually finished. The first logon went through another very brief intro to the user interface.
Despite being configured to install the latest firmware, it did not. Turns out there is still newer firmware, SRM version 1.2.3-8017 Update 2 which was released August 2019. It's not you, these version numbers are indeed ridiculous. I upgraded again.
The new firmware chose yet another channel on the 5GHz band (36), which is fine, but switched to channel 2 on the 2.4GHz band, which is just as bad a choice as channel 8. Clearly Synology did not get the memo about sticking to channels 1, 6 and 11 which benefits everyone.
There is a new Wi-Fi management interface called Wi-Fi Connect. Great news: the new release lets you set both your desired Wi-Fi channel and channel width while still having one SSID that covers both frequency bands. It shows new WPA3 options, including a new OWE option. But, it still supports WEP. The wireless mode is still forced to Auto and what that means is not explained. Anywhere. Yes, I did read the Help, there is nothing there.
The CPU usage display is still buggy with a huge difference between the graph and the Load Averages. How does no one notice this?
At this point I realize I don't know how to contact tech support. I read the SRM Help section on the Support Center. Still, I could not figure out how or who to ask for tech support. In fairness, the Quick Installation Guide says to go to sy.to/support for questions and this forwards to www.synology.com/en-us/company/contact_us. In addition, there is a Support Center app in the web interface that is hidden by default. To see it, click the Main Menu icon in the top left corner.
That said, when I tried the Support Center app, it did not work, failing to phone home to a Synology server. And, the failure was not logged. Turns out, the problem was the Privacy Badger browser extension from the EFF. It blocked access to account.synology.com. I wonder why.
POKING AROUND THE UI top
The Synology NAS operating system (DSM) has a logging app, that seemed to be missing from SRM. I was looking for this because, as a security measure, I like to audit any time someone logs on to the router. I say "seemed" because I found the app by searching. In what I consider a design flaw, some of the pre-installed apps are on the SRM desktop and some apps are not. Those that are not, are available in the Main Menu thingy in the top left corner. And, it was in the Main Menu where the log app lives. I don't know why Synology doesn't put all the pre-installed apps on the desktop, there is plenty of space. You can copy icons from the Main Menu to the desktop and I suggest doing so. Others apps only available in the Main Menu were the Security Advisor, Network Tools and File Station.
Good news: it does log every login to the web interface and the log includes both the userid and the source IP address. Which reminds me, SRM supports more than one userid. It might be a good idea to create two, just for good luck.
Bad news: it is generating warning messages that I do not understand.
"Failover event triggered, switch (ipv6) network default gateway to (wan)"
"Failback event triggered, recover (ipv6) network default gateway to (wan)"
Similar messages were also generated for IPv4. I have no clue what this is about.
Even without understanding them, the messages were helpful, as they showed that IPv6 was enabled. I don't think any home user need IPv6, so as part of lowering the attack surface, I turn it off whenever possible. To disable IPv6: Network center -> Internet -> IPv6 button.
Funny story about the context sensitive Help in SRM. It wasn't working. I could search for something, see the list of topics, but the actual help was blank. It was funny because this was caused by the Privacy Badger extensions from the EFF. It had blocked www.synology.com as a potential tracker. When I modified Privacy Badger to allow the synology web site, the Help information returned. Privacy Badger also blocked synoform.synology.com but I didn't notice anything breaking because of it. This makes me wonder, what the EFF saw that made them consider that Synology was spying on me.
When you run the Security Advisor app you are asked if you are a person (Home and Personal use) or business. Synology profiles people as needing less security than businesses. When run for a person, it said that all users have strong passwords. The one user had a six character password, not all that strong.
Unlike most routers, SRM supports multiple users. The router ships with two pre-defined userids, both disabled by default: admin and guest. Chances are one userid is enough, but it can't hurt to define a second user, just in case. They don't say, but my testing showed that userids are not case sensitive.
Bad news: I created a second user and logged on with it, only to find that that it was limited to running File Station a NAS app. None of the router apps were visible, even in the Main Menu. Totally worthless. Nowhere in the process of creating this new userid did it say anything about limiting what it could do. Looking at the two users at Control Panel -> User (while logged on as an Admin user), they look identical. The context sensitive Help says nothing about this. The only options for users that it discusses is access to shared folders. Not sure what's going on here.
Speaking of users, at Control Panel -> Services -> Application Privileges you see that all users get access to FTP, File Station and WebDAV. Not good for security and not really relevant to a router.
When I then ran as a business, there were more warnings. An important warning was that Auto Block was disabled. This is the feature that locks down the router after someone has entered an invalid password too many times. While I was glad for the warning, it is yet another case of insecure out-of-box defaults. You enable and configure Auto Block at Network center -> Security -> Auto Block tab. Another warning was about bad passwords. SRM can impose rules that I was not using: enforcing mixed case, numbers and special characters. It also complained that the automatic re-directing of HTTP to HTTPS was disabled, which leads to the next topic.
The Network Center Status does not show the signal strength for devices connected by Wi-Fi. It also does not show the SSID that wireless clients are connected to. The default identifier for client devices is almost always useless, for all routers. From the Device List on the status page you can not rename a device with a name that makes sense to you (Bobs iPad, Carols laptop). The router lets you do this, I saw it once, not sure where. When I remotely logged into the router, the Device List in the Status display did not show me as connected user.
Support Center app: The Support Services tab has a checkbox for "Enable remote access" that allows Synology support engineers to access the router. It is great that they offer this feature, I have not seen it on any other consumer router. Peplink offers it too. I turned on the checkbox, clicked the blue Apply button and after 10 seconds or so, the checkbox was unchecked again. There was a message that said "Setting Applied" in green, yet the setting was showing as off. At no point was the "Access valid until" field filled in and its not clear what the required "Support identification key" is. Also, it does not say what ports are used for this feature. I ran an nmap scan and it did not open any additional ports. The only two ports open on the WAN side were my customized ports for HTTP and HTTPS. Sloppy.
Denial of Service protection: Network center -> Security -> General tab has a checkbox for DoS protection that is off by default. I turned it on and suggest anyone does. There may be a downside but I don't know what that would be. It claims to protect against TCP reset attacks, SYN floods and ICMP floods. Testing this is beyond me.
EXTERNAL ACCESS PORTS top
External access to the router is configured at Control Panel -> System -> SRM settings where there is a checkbox called "Allow external access to SRM". There was no default, I was asked about this during the initial setup. The more secure option would be to disable this by default as every other router does. Many users have no idea what this means and it is not explained during the initial setup. These customers should be protected from themselves with secure defaults.
The description says that it allows both HTTP and HTTPS. This is true. Nmap against the WAN port shows that both the non-standard HTTP and HTTPS ports that I configured are open. SRM is not able to limit remote access to HTTPS. No one wants to allow remote router access via HTTP. This is very poor security, even for a consumer router. But not unique. I once bought a Netgear router for someone I know and ended up returning it once I realized that it could not restricted remote access to HTTPS.
The checkbox description also mentions ports 8000 and 8001, despite the fact that I had changed these ports and they no longer work. This is a double mistake as the option to change the ports used by the web interface is not right here. It's somewhere else. Where? Dunno. I am worn out trying to find things in the user interface. Nothing seems to be in the section where I expect it. At one point I disabled Windows Network Discovery. Later, I wanted to find the option again, but I could not. Your mileage, of course, will vary.
One guess was Network Center -> Security -> Firewall tab. It makes a bad first impression in that it does not say if its for an inbound or outbound firewall. Whoever designed this apparently thinks firewalls only work in one direction. :-(
Worse still, I can not understand how to configure the firewall. It's not my first firewall, I've been down this road before. For example, it says "If IPv6 WAN to SRM traffic matches no rules" and lets you Allow or Deny. What rules? There is also a choice for WAN to LAN traffic. An inbound firewall rule usually offers a Yes or No choice. This seems to be offering two inbound choices, one for traffic to the router, another for traffic to the LAN. And, the one for traffic to the LAN is Allowed by default. WTF?
If you look below, in the section on Spying on the Router, you will see a screen shot of an outgoing firewall rule from my Pepwave router. Everything it is doing is simple, clear and obvious.
My guess is that this can block inbound HTTP, but that's just a guess. If it can, we now have parameters for external access to the router in three different places. Poor design. Oh, and you configure the HTTP and HTTPS ports at Control Panel -> System -> SRM settings. I found this by searching for "ports". It was the 4th search result.
Somewhere there is an option for HSTS that says it forces all browsers to use HTTPS. It does not. I was able to use HTTP for remote access to the router even with HSTS turned on.
LOCAL ACCESS PORTS
Local access was also problematic, but for different reasons.
Let me take a step back. The whole idea with configuring the TCP/IP ports used for the web interface is security. Normal website ports are 80 for HTTP and 443 for HTTPS. If someone or something malicious gets on your network, you do not want them to be able to use ports 80 or 443 to access the router. Think of a non-standard port as a poor man's password. You want to block anyone who does not know the port number from connecting to the router. This can't fully block someone but it does make the attacking person/software guess amongst 65,000 ports before they even get prompted for a userid and password. It is not ironclad security, but it is another barrier for an attacker to get over.
And Synology can not do this. While it does let us change the ports used for HTTP and HTTPS, there is no benefit, as it does not block access to ports 80 and 443. You can see this two ways. One is with nmap run from a computer connected to the router. Ports 80 and 443 always show up as open. You also see it with a web browser. Both HTTP and HTTPS requests to router.synology.com should, with a more secure router, fail, because each uses the default TCP port. But, with the RT2600ac these commands do not fail. Instead:
http://router.synology.com ---> redirects to http://router.synology.com:8888 where 8888 was my alternate HTTP port.
https://router.synology.com ---> redirects to https://router.synology.com:9999 where 9999 was my alternate HTTPS port.
In effect, the router is advertising to attackers what your non-standard ports are. That, stinks.
The icing on this cake comes if you make an HTTP request with your browser to the HTTPS port. In this case, the RT2600ac is very helpful, telling you: "Your browser sent a request that this server could not understand. Reason: You're speaking plain HTTP to an SSL-enabled server port. Instead use the HTTPS scheme to access this URL, please." Helpful is not secure; I want this request to fail.
There are other ways to restrict access to the web interface. Synology does not offer restrictions based on IP address, MAC address or Ethernet connections. However, it does support two step verification (aka 2FA, two fact authentication) using an authenticator app. I did not test this.
Google Analytics in SRM
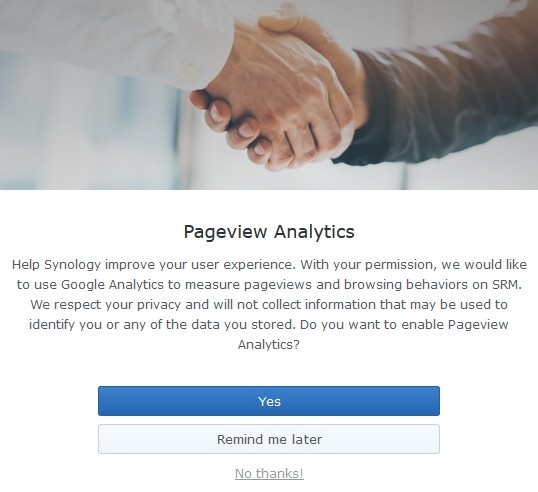
GOOGLE ANALYTICS
One of the new features is troubling. Synology introduced Google Analytics to, in their words: "measure pageviews and browsing behaviors on SRM". Netgear did the same thing and opted customers into their spying/analytics by default. Synology asks if you want to participate. They use the now standard yarn about why they are doing this - to help them improve your user experience. Everyone says that before spying on you.
Synology has bragged about the security features in their routers, but if they were really serious about security, they would not be installing Google Analytics in their web interface. In fairness, everyone does it. I have even seen VPN providers ask about enabling analytics when installing their software.
To check the status of Google Analytics: Control Panel -> System -> SRM Settings tab. A link to their Privacy Statement is there too.
GUEST WIFI NETWORK top
The Guest network is configured with the Wi-Fi Connect app -> Guest Network.
Like the main/private network, there can either be one SSID that spans both frequency bands (Smart Connect on) or each band can have its own unique SSID (Smart Connect off).
The Guest network defaults to the 192.168.2.x subnet, with the router on 192.168.2.1. You can change the DHCP range, but the router IP address is fixed. It does not look like you can change the subnet, but you can. Change the DHCP range to one in another subnet and SRM will adjust the gateway IP address to be the dot one in that subnet. I found this out with trial and error. If you create two Guest networks, they both share the same subnet.
The security of the Guest network is excellent.
- An issue with all Guest networks is access to the private network. There is a checkbox to "Allow guest to access my local network". It is off by default.
- Guest users are isolated from each other. I ran three LAN scanning programs when two devices were on the Guest network. Each scanner saw only itself and the router. None detected the other Guest user.
- Guest users can not access the web interface of the router. I tried HTTP and HTTPS. I tried the default ports and my customized ports. I tried router.synology.com. I tried the Guest subnet and the private subnet. Everything failed.
- Guest users see no open ports on the router. This is a drastic contrast from the private network where devices see a dozen or so open ports on the router.
- Guest users can not Ping the router at either the Guest subnet or the private subnet.
Scheduling options for the Guest network are robust. You can have it live for 1 hour, 3 hours, 8 hours, a day, or a week before being disabled. If you know where to look, SRM even shows the time remaining. Want more control? You can customize a schedule for every hour of the week. For example, the Guest network might be enabled from 8AM to 6PM on weekdays, from Noon to 4PM on Saturday and off on Sunday.
The router can rotate the Guest network password on its own. It generates the passwords, you can not provide them. It can create easy, medium or hard passwords. You set the schedule for when the password should be changed. How do you know what password it's using? The router will email it to you. This requires that you first enable the email notification feature.
Taking these two features together, Synology could be a great choice for a small business that needs to provide Wi-Fi and only has a part-time IT person.
It let me enable the Guest network without first picking a password. Just like the Wi-Fi network that the router creates when it starts up the first time, there was a default password of "synology".
Good news: You can limit the number of concurrent connections to the Guest network. Bad news: there are very few choices: 1, 16, 32 and up. Having to chose between 1 and 16 makes this feature mostly useless, except if you have one and only one guest. I verified that it works.
The Guest network enables Wi-Fi G, N and AC. Nowhere are you told this or given the option to configure it. I discovered this use a Wi-Fi scanner app. I have to assume the Guest network inherits this from the private network.
WPA2 Enterprise is not supported on the Guest network.
An Android 8.1 device incorrectly complained that the WLAN had no Internet access when connected to the Guest network.
There is an option for the Guest network called "regional compatibility" I can't guess what this is, and there is no documentation on it.
The software offers WPA3 encryption options, but the Help page has not been updated to reflect this.
You can run a captive portal on the Guest network.
You can have a Guest network only, no need to also have a private Wi-Fi network. However, SRM gets confused with this. At Network center -> Status the display will be wrong. It will say that Wi-Fi is disabled when it is not.
The MAC address of the private network starts with 00:11:32 which is assigned to Synology. On the Guest network, the MAC address starts with 02:11:32 which is not assigned to anyone.
When a guest network is first enabled, it is always unscheduled. After enabling it, and waiting, you have to then go into the scheduler feature to limit its life span. The user interface for configuring the Guest network is spread out. The controls I used were in three different places.
Wi-Fi Connect -> Guest Network -> Wi-Fi tab
Wi-Fi Connect -> Guest Network -> Schedule tab
Network center -> Local network -> General tab -> Guest DHCP server
In configuring the DHCP range for the Guest network, there were two options I was not familiar with: "Forward known DNS server" and "Domain name". I read the description of each and it made no sense. I am no world class expert, but I am reasonably familiar with this stuff.
Two other parameters that I am not familiar with are IGMP Snooping and IGMP Proxy. There is no documentation about them either.
I thought I knew what NAT was, but it can be enabled or disabled for DHCP, so I clearly do not know what it is. Again, no documentation on what it means to Enable to Disable NAT.
VPN CLIENT top
Out of the box, the RT2600ac can function as a VPN client. It can connect to three types of VPN servers: OpenVPN, L2TP/IPSec and PPTP. I tested this using OpenVPN to connect to a Mullvad server. Results were sub-optimal. I had one big issue along with many minor gripes. The big problem was that, at first, nothing was actually using the VPN even though the router said it was connected. Mullvad officially supports routers running DD-WRT, OpenWrt, PfSense, Asus Merlin and Tomato. But, OpenVPN is standardized to the point that they said a Synology router should work. And it did, sort of.
To get to the VPN client, go to Network Center -> Internet -> Connection tab (the default) and click the gray VPN Settings button. The Create button creates a new VPN connection profile. One connection profile goes to one VPN server, so if you want to use three VPN servers, you will need three profiles.
There are two logic paths; one requires importing a .ovpn file, the other does not. I opted to start without importing an .ovpn file. Both logic paths require you to upload a certificate in a file to the router. Strange that this is required when using an .ovpn file as the ones I have seen include the certificate. In fact, to get the required certificate I copied it out of an .ovpn file into a file by itself.
When not importing an .ovpn file, you need a user name and password for your VPN provider, the VPN server name (or IP address) and the server port number. You also have to answer three questions.
- Enable compression on VPN link?
- Use default gateway on remote network?
- Reconnect when the VPN connection is lost?
Compression was on by default, the Default Gateway and Reconnecting were off by default. I can not imagine why anyone would not want to re-connect automatically. The Synology VPN client documentation offers no clue.
What the documentation does offer is an option that did not exist: "Allow other network devices to connect through this Synology server's Internet connection." When was the documentation last updated? None of our business. What version of SRM was it written for? None of our business. Reference to a "server" makes me think the option applies to NAS boxes and the documentation was just copied.
My first attempt connected, but there was much to dislike.
For one thing, there was no message log. Other routers show this log which is needed for debugging when something goes wrong. Synology does not make the connection log available. Later I needed the log as other attempts at establishing a VPN connection failed. Why? None of my business. One failure was "Connection failed. Please check your network settings," the other was "Failed to establish network connection." Seeking help, I checked the router logs. It logs the creation of a new VPN profile and, should you rename the profile, it logs that too. But the details of a connection failure are none of your business. Clearly the VPN client software is not ready for prime time.
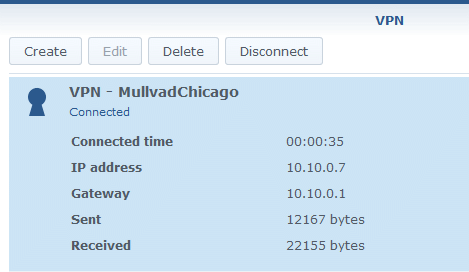
VPN connection status
I noticed two other things while trying to debug connection failures on my own. Once you enter the password for your VPN account, you can never see it again. Same with the digital certificate, the router does not even confirm that you ever uploaded a certificate at all, let alone display anything useful from it.
The lack of useful information continues when you have established a VPN connection.
For one thing, there should be an indicator light on top of the router showing that it has a VPN client connection. It also needs to tell you the name or IP address of the VPN server that it has connected to. How could anyone have thought that making this a secret was a good idea? The IP address shown here at the right is on the VPN providers internal network. No one cares about this. The gateway IP is also on the VPN providers network and not of any use. Even when it shows some information, it is done in a bad way. Note the bytes sent and received at the right. Yes, bytes. Not megabytes or gigabytes, just plain bytes. Heck, there aren't even any commas. And to get to this data you have dig down four levels in the web interface.
The same holds true for the main Status display at Network Center -> Status. Whereas it normally displays the public IP address, when connected to a VPN it shows the IP address assigned the router on the internal network of the VPN Provider. Same for the Gateway IP address. The displayed IP address of the DNS server is a fiction; it too, is internal to the VPN provider network rather than a public IP address on the Internet. It is not the IP address that devices connected to the router are assigned.
It seems as if no thought went into designing the VPN client.
By the way, there are many websites that show the DNS servers your computing device is actually using. I have a list of them on my RouterSecurity.org website, on the Test Your DNS page.
After making my first VPN connection, I ran a trace route to confirm that it really was connected to the remote VPN server. The trace route started in my home city rather than the city where the VPN server was located. Something was wrong.
I had taken all the defaults for the three questions and one of the defaults was a huge mistake. The option "Use default gateway on remote network?" defaulted to OFF. Turns out it has to be enabled. I can't imagine why this is even an option. Who would want to connect to a VPN server and then not have devices connected to the router use the VPN connection?
While connected to a VPN, you can not look at the properties of the VPN profile. The Edit button is disabled.
After using a VPN for a while, I checked the Log Center app to see what was logged. At one point there was a log entry that said "VPN connection disconnected by user." One second later, there was a long entry that said &qupt;VPN connection was disconnected by the server". Which is it? That a user disconnected is just an FYI. That the server disconnected is considered a warning. Makes no sense to me.
CONNECTING WITH AN OVPN FILE
To generate an ovpn file with Mullvad you have to lie to their website and say the target OS is Linux. As noted above, their ovpn files include a certificate which I had to copy into its own file. This second logic path for configuring an OpenVPN profile also requires a Certificate in a file by itself. And, it asks two questions, whether you want to use the default gateway on the remote network and whether to re-connect should the VPN connection drop. Both default to NO and I changed each to YES.
The newly defined VPN profile connected. And then trouble.
The main Status display (in the Network Center app) said Limited Connection. The VPN display showed data flowing in each direction, so I don't know what to make of this. Shortly, the main Status reverted to displaying the non-VPN IP addresses. Yet, this conflicts with the VPN app which said the VPN was connected. Clearly a bug. Maybe two. The Status display in the Wi-Fi Connect app said "Failed to access the Internet" which also conflicts with what the VPN app which still says it is connected.
The user interface makes this impossible to debug. It displays nothing about the ovpn file. Heck, it does not even acknowledge that there is an ovpn file. Whatever parameters were configured in the ovpn file are not displayed anywhere.
Not wanting to deal with a system that seems confused, I disconnected the VPN and rebooted the router to get a fresh start.
xxxxxxxxxxxxxxxxxxxxx Limited connection again yet status shows some data flowing in each direction check vpn and it has connected to the vpn from the ovpn file. why? I had disconnected it just before rebooting. disconnecte the vpn and rebooted the router a second time next Limited connection with VPN IP addresses in main Status (network center) after a minute, it gave up on the VPN IP addresses and went back to the non vpn environment. sure enough, the vpn shows as connected, which direclty connects with IP address in status. clearly a bug I manually disconnect and change the option about reconnecting. then reboot for a third time. still limited connection and the Status shows public IPs not the VPN IPs. VPN app says it is connected. What a freaking mess. then no more limited. all happy. vpn app still says it is connected log center app shows the vpn connecting just after the router starts up. why??? then Failover event triggered, switch (ipv4) network default gateway to (wan) confirms vpn disconected before rebooting connect a pc ot the router .... whats its ip ??? VPN ip dsn servers also came from VPN provider network tools -> Traceroute shows the location of the vpn server, Network center status is WRONG. no way to stop this third vpn profile from auto-connecting. I deleted this vpn profile.Finally, lets talk VPN speed.
Using Fast.com, I tested the speed with the VPN connected three times from a Wi-Fi connected tablet and got readings of 10, 9 and 19 Mbps. Then, with the VPN disconnected, I saw speeds of 31, 16 and 23 Mbps. As expected, the VPN slows things down.
Days later, another test using an Ethernet connected PC and the speedtest.net website. Speedtest correctly determined the city where the VPN server was located and tested using a server in that city. Download speed tested at 17 and 21 Mbps a few minutes apart. Since the Synology router is connected to my Pepwave Surf SOHO, I also checked the speeds on the Surf SOHO. During the second speed test, it reported a maximum download speed of 23 Mbps. With the VPN disconnected, the Speedtest website still insisted on testing with a server in the VPN server location which is over a thousand miles from me. Nonetheless, download speed was 88 Mbps. I restarted the browser and forced the speed test to use a server in my city. The result was exactly the same, 88 Mbps. In both cases, the Surf SOHO router showed a peak download of 91 Mbps, which is just about as fast it can go.
While I expected a slowdown, going from 88 to (an average of) 19 Mbps seemed a bit much. Perhaps the one VPN server was over-taxed? I connected to a different VPN server and again tested at the speedtest.net website using a test server in the same city as the VPN server. Download speed was 19 and 21 Mbps a few minutes apart. On the whole, the speed decline on the VPN was about 77 percent when connected via Ethernet.
The slowness on a VPN is due to three factors: the extra transmission hop to get to the VPN server, resource contention at the VPN server and the CPU horsepower of the router. There is no great way to measure, as far as I know, which of these factors is the largest contributor. However, I had a hunch that much of the speed decline was due to the router itself. I say this because I have previously seen speed tests over 80 Mbps while connected to Mullvad.
To test my theory, I used the same Ethernet-connected PC in two other tests: directly connected to the Internet and directly connected to a Mullvad server in one of the cities I had just tested. That is, I connected the PC directly to my Surf SOHO router, ran speed tests, then used the Mullvad Windows software to connect to their VPN service and tested again.
Connected to the Surf SOHO without a VPN, the speedtest.net site reported speeds of 87 and 86 Mbps a few minutes apart. The tests were against two different servers in the same city as the router. Then, connected to Mullvad via their software, the PC tested at 76 and 80 Mbps a few minutes apart. Here too, the speed test used a server in the same city as the VPN server. Clearly, the router is a huge part of the slowdown when using an OpenVPN server. You might think to look at CPU usage in the router during the speed tests but that was the first bug I noticed after powering on the RT2600ac. I don't know which of the very divergent numbers the router reports are correct.
In summary, for this one Ethernet-only PC
- Directly connected to the Internet: 86 Mbps
- Connected to Mullvad via PC software: 78 Mbps
- Connected to Mullvad by the Synology RT2600ac (no PC software): 20 Mbps
LAN SIDE NMAP AGAIN top
The RT2600ac is connected to my Pepwave Surf SOHO. The WAN port of the Synology goes into a LAN port on the Pepwave. This lets me run nmap against the WAN port of the RT2600ac from a computer connected to the Pepwave. I scanned the Synology router for all 65,535 TCP ports. The result was perfect, they were all filtered. This, I believe, is normal for routers that are not provided by an ISP.
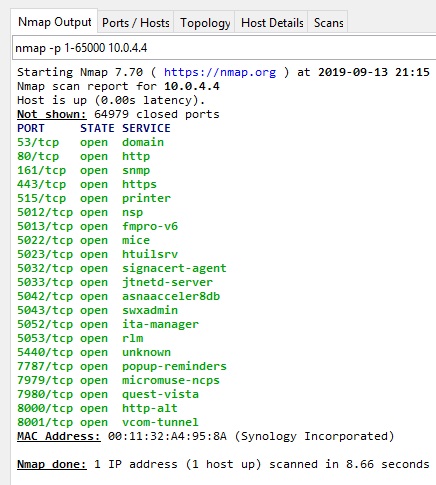
nmap scan of the LAN side
Open ports are not the only issue on the WAN side, so too is Ping Reply. It's not the most important feature in the world, but not responding to Pings makes a router a bit more hidden on the Internet. If you care about security, you don't respond to Pings. If you prefer to use Pings for network testing, then you do reply. I searched and searched and could not find a configuration option for this. On the LAN side it did respond to Pings, on the WAN side it did not.
The LAN side nmap results were the total opposite of the WAN side. Shown at the right, the LAN side of the router has more holes than Swiss Cheese. Specifically, nmap found these ports open: 53, 80, 161, 443, 515, 5012, 5013, 5022, 5023, 5032, 5033, 5042, 5043, 5052, 5053, 5440, 7787, 7979, 7980, 8000 and 8001.
The last two ports are used by the web interface on the LAN side; 8000 is for HTTP and 8001 is for HTTPS. This raises the question however of why 80 and 443 are also open.
Nmap can sometimes detect the software running behind an open port. Port 53 is running dnsmasq, at the same version (2.78) as the older edition of SRM. Dnsmasq is also running on port 5440. 80 and 443 are running the Apache web server. Apache is also running on ports 5012, 5013, 5022, 5023, 5032, 5033, 5042, 5043, 5052 and 5053. Detection failed for ports 161, 7787, 7979 and 7980.
My one attempt to close some ports was disabling Windows network discovery. This seems to have closed two ports: 7979 and 7980. It is never secure to use the default ports for the web interface, so I changed both the HTTP and HTTPS port. I also disabled HTTP support by turning on the option to re-direct HTTP requests to HTTPS.
Then, I ran into documentation on ports from Synology: What network ports are used by SRM services? The document is disappointing in three ways. First, it has no last update date. Second, it does not say which version of SRM it applies to. Third, it is incomplete. As for what it says:
- Port 80 is not used at all. So, why is it open?
- Port 161 is used by SNMP which I did not specifically enable. The secure choice is to disable SNMP by default.
- Port 443 is used by VPN plus which is neither installed nor configured
- Port 515 is on the list for UDP, but I found it open for TCP.
- Port 5440 is used by Parental Control which I never turned on
- Ports 5012, 5013, 5022, 5023, 5032, 5033, 5042, 5043, 5052 are 5053 used by Safe Access. I never turned this feature on and don't know what it is. That said, it is the very opposite of "Safe" to open ports by default.
- Port 7787 is associated with a Mesh network, which I am not using. It also has to do with LBD, whatever that is.
- Ports 7979 and 7980 are not on the list at all. A mystery.
I did some more checking. Just as with the out-of-box version of the firmware, SNMP still appears to be off. There is a checkbox for it at Control Panel -> Services -> System Services tab. So, why is its port (161) open?
Safe Access deals with profiles and I have not created any. It also has a network protection feature that is off, so it beats me why it has opened so many LAN side ports. The Safe Access app (again, called a package) is running. So, I stopped it, hoping to close the many ports it is using. Stopping the app, removes it from the visible web interface. Not only does its icon disappear from the desktop, it also is removed from the Main Menu. Out of sight out of mind, it would be better if the icon remained but the interface made it obvious that it was disabled. As for the LAN side ports ...
SPYING ON THE ROUTER top
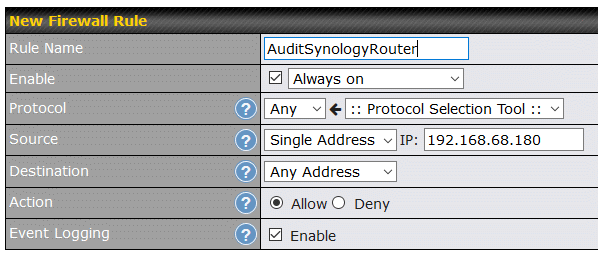
Auditing Outbound connections
Usually the router spies on us, but in this case, I am spying on the router. To do so, as described above, the WAN port of the RT2600ac is Ethernet connected to a LAN port on my Pepwave Surf SOHO. The outbound firewall rule, shown at the right, on the Surf SOHO lets me allow and log every outgoing connection made by the Synology router.
If a computer connects to the Synology router and requests a web page, the Surf SOHO will see that and log it. Boring. Instead, I powered on the Synology router and waited. Nothing connected to the Synology router at all. Not one device. I wanted to see if it phoned home. The last time I did this, it was to another Surf SOHO router and all I saw were connections for the time of day (NTP on UDP port 123).
There are a number of reasons for a router to phone home; good ones and bad ones. The time of day is a good one. The Pepwave Surf SOHO phones home to 0.pepwave.pool.ntp.org to keep track of the time. Another reason is to verify that the router has a working connection to the Internet. Peplink (the company that makes Pepwave) routers offer four methods for checking their online status and each method has multiple configuration parameters. Routers that can self-update have to periodically phone home to check for software updates.
Detailed activity logs are here in plain text format.
PING HAPPY
The first thing I noticed was the router was addicted to Ping, a simple network command used for testing connectivity. It does a lot of Pings. I can only guess that this is done to test if the router has a working connection to the Internet. It pings the main Google DNS server at IP address 8.8.8.8. I'll bet Google does not appreciate that. You would think Synology could Ping one of their own servers. Ping shows up in the Pepwave Event Log as ICMP type 8.
I saw 6 pings the first minute that logging was active, then 3 in the next minute, 6 in the minute after that and 6 again in the next minute. This was followed by another 6 in the next minute, and 3 in the minute after that.
These were flooding the Event Log with boring data. So, I made a new firewall rule that both allows these Pings and does not log them.
TIME OF DAY
Again, the log was flooded with boring data. This time, it was requests for the time of day. More specifically, NTP requests to UDP port 123 from port 123. The RT2600ac makes tons of these requests. Here too, Synology is not providing their own NTP server, the requests were to many different IP addresses such as: 23.31.21.164, 172.98.193.44, 204.11.201.10, 138.68.46.177, 45.56.74.200, 45.63.54.13, 104.236.116.147, 69.164.213.136, 129.250.35.251 and 45.63.54.13. Checking Control Panel -> Device -> System Information shows that the router is using pool.ntp.org as its time server.
Again, full log details for just over an hour are here in plain text format.
As with the Pings, I made a new firewall rule that allowed this traffic and did not bother logging it.
There does, however, seem to be a problem with the Pepwave router assigning an IP address to the Synology RT2600a. Whenever possible, the Pepwave assigns the same device the same IP address, which makes this logging easier. But, it has to assign the IP address multiple times. Here is an excerpt from the Pepwave Event log as the Synology router was powered on:
16:50:28 DHCP Server: 192.168.68.99 assigned 192.168.68.180 to 00:11:32:a4:95:89, lease time 86400
16:50:18 DHCP Server: 192.168.68.99 assigned 192.168.68.180 to 00:11:32:a4:95:89, lease time 86400
16:50:00 DHCP Server: 192.168.68.99 assigned 192.168.68.180 to 00:11:32:a4:95:89, lease time 86400
16:49:34 DHCP Server: 192.168.68.99 assigned 192.168.68.180 to 00:11:32:a4:95:89, lease time 86400
Four assignments of the same IP address in roughly a minute. Lease time is duration of the IP address assignment in seconds and a full day is 86,400 seconds. I don't know why this has to happen four times, but I did check the Pepwave router and it has not had any dropped packets on the LAN side. From what I have seen, Synology does not report dropped Ethernet packets.
THIRD TIME IS A CHARM
With the boring traffic no longer being logged, what's left is interesting.
Again, these activity logs are from a router with no connected devices. I powered the thing on and just watched the outbound connections it made. What I forgot was to disable any and all checking for updates which the RT2600ac does a lot of. Not only does it check for firmware updates, it also has assorted databases that, by default, check for updates to themselves. You see this at Control Panel -> System -> System Database. The databases are for Threat Intelligence, Google Safe Browsing, Domain Names and IP Geolocation. Later, will do this same logging with all the self-updating disabled.
When I first discovered these databases, their self-updating seemed not to be working. Each was set to "Automatically check for an install updates" yet two of them said "Newer version available" with a blue Update button. Clicking the button updated them just fine, but I don't know why they didn't automatically update.
Although I installed no additional software (aka apps, aka packages) the Safe Access app was pre-installed and enabled. Apps installed on the router are yet another thing that can be auto-updated. The default, however, is not to automatically update them. You set this at: Package Center -> Installed -> Settings button -> Auto Updates tab. However, not auto-updating is different from not checking for updates. You will see below that the router does phone home to update.synology.com, despite all my attempts to the contrary.
As for what we can expect in terms out outgoing connections, Synology publishes What websites does Synology NAS connect to when running services or updating software? for their NAS devices. There does not seem to be a similar page for their routers. Similar to the above, they also publish What network ports are used by Synology services?. Again, this is for DSM, their NAS operating system, not for their routers.
There are three issues here:
- Why does the router keep phoning home to Synology even though self-updates have been disabled?
- Is the router contacting anyone other than Synology?
- What data is the router sending out?
September 17, 2019
The router was powered on at 37 minutes after midnight and nothing connected to it. Below are the important parts of the log of its outgoing connections. DST is the destination IP address. DPT is the destination port and SPT is the source port. All connections use TCP, had there been any UDP traffic, it would have been logged. Most of the traffic occurred whle the router was starting up.
Sep 18 18:00:04 DST=99.84.176.197 SPT=60878 DPT=443
Sep 18 18:00:03 DST=99.84.181.17 SPT=39776 DPT=443
Sep 18 18:00:03 DST=99.84.176.197 SPT=60874 DPT=443
Sep 18 15:23:02 DST=54.230.195.142 SPT=43560 DPT=443
Sep 18 15:23:01 DST=52.60.32.222 SPT=38262 DPT=443
Sep 18 11:20:41 DST=210.61.203.210 SPT=50384 DPT=443
Sep 18 06:08:45 DST=210.61.203.210 SPT=50382 DPT=443
Sep 17 22:33:04 DST=210.61.203.210 SPT=50380 DPT=443
Sep 17 18:00:03 DST=13.249.47.215 SPT=55552 DPT=443
Sep 17 18:00:03 DST=13.249.44.37 SPT=52870 DPT=443
Sep 17 18:00:03 DST=13.249.47.215 SPT=55548 DPT=443
Sep 17 15:24:32 DST=210.61.203.210 SPT=50372 DPT=443
Sep 17 15:23:01 DST=13.225.224.105 SPT=41242 DPT=443
Sep 17 15:23:01 DST=99.79.3.38 SPT=57264 DPT=443
Sep 17 06:58:06 DST=210.61.203.210 SPT=50366 DPT=443
Sep 17 00:43:02 DST=210.61.203.210 SPT=50364 DPT=443
Sep 17 00:39:36 DST=68.183.161.151 SPT=39508 DPT=81
Sep 17 00:39:29 DST=13.225.68.230 SPT=57620 DPT=443
Sep 17 00:39:29 DST=13.225.62.58 SPT=51292 DPT=443
Sep 17 00:39:29 DST=13.225.68.230 SPT=57616 DPT=443
Sep 17 00:39:27 DST=68.183.161.145 SPT=53158 DPT=81
Sep 17 00:39:27 DST=13.225.68.230 SPT=57612 DPT=443
Sep 17 00:39:26 DST=13.225.212.129 SPT=57056 DPT=443
Sep 17 00:39:26 DST=13.225.68.230 SPT=57608 DPT=443
Sep 17 00:39:23 DST=178.128.11.127 SPT=33446 DPT=81
Sep 17 00:38:57 DST=178.128.11.127 SPT=33444 DPT=81
I used Shodan to research these IP addresses. It shows the name of the computer at each IP address and, for secure websites, it dumps information from the certificate the computer served up on port 443. Normally, the company that the certificate was issued to, is in charge of the computer at that IP address. Shodan queries look like:
https://www.shodan.io/host/1.2.3.4 where 1.2.3.4 is an IP address.
These IP addresses appear to belong to Synology:
- 210.61.203.210 is synology.com in Taiwan
- 13.225.68.230 is update.synology.com
- 13.249.47.215 is update.synology.com
- 99.84.176.197 is update.synology.com. Security trails says it is update.synodns.com.
- 99.79.3.38 is payment.synology.com
- 52.60.32.222 is payment.synology.com
- 68.183.161.151 is on-us-checkip4.synology.com at Digital Ocean in the US. There was no certificate as it was contacted on port 81.
- 68.183.161.145 is on-us-checkip3.synology.com at Digital Ocean in the US. Again, port 81 so no certificate.
- 178.128.11.127 is on-us-checkip2.synology.com at Digital Ocean in the US. Again, port 81 so no certificate.
The use of port 81 is strange. I don't know if the outgoing data was encrypted as I did not run a packet capture. And, since there no documentation on expected activity from the router, there is no where to verify it.
According to the data in the certificate on port 443, these IP address do not appear to belong to Synology. For a second opinion on them, I also checked SecurityTrails.com.
- 13.225.62.58 is www.accacareers.com. The certificate also contains these alternate names: cnjobs.accaglobal.com, www.accacareers.ie and more. The server is from Cloudfront and hosted at Amazon in the US. For reasons I do not understand, a later Shodan query reported a certificate issued to cityofpenitas.com. Security Trails found no websites at all for this IP address.
- 13.225.212.129 is cdn.technolutions.net. The server is from Cloudfront and hosted at Amazon in the US. The response on port 443 also included this: "HTTP/1.1 302 Moved Temporarily Location: https://www.mtholyoke.edu/admission/" For reasons I do not understand, a later Shodan query reported a certificate issued to anydesk.com. Security Trails says that 13.225.212.129 hosts www.residencyhealth.com, zcw166.com and zcw32.com.
- 13.225.224.105 is forums.rotoworld.com. The server is from Cloudfront and hosted at Amazon in the US. For reasons I do not understand, while verifying this, the certificate changed and the new one is myonlinecamp.com. Security Trails said that 13.225.224.105 hosts ah7575.com, d2dzl9m3tzyylt.amplifyapp.com, d1eeyt7z9xdnzd.cloudfront.net, eusoumanaus.com.br, golagola.com, www.nickjonas2019.com and testedtough.net.
- 13.249.44.37 is cassandrasummit.org. The server is from Cloudfront and hosted at Amazon in the US. The certificate is also valid for thinkaurelius.com. Security Trails says this IP address hosts 4,962 websites.
- 54.230.195.142 is beta.channeladvisor.com. Security Trails has there are over 13,000 domains on that IP address.
- I can not even guess what 99.84.181.17 is. The certificate did not display correctly at Shodan. Security Trails says there are 7,600 domains on that IP address.
There is something going on with these Cloudfront servers that I do not understand. One guess is that with multiple virtual servers living on the same IP address, Shodan queries get a random response from the server because they do not include the name of the desired server/website.
BOTTOM LINE
I brought this up with tech support at Synology. They were responsive and intelligent in their replies. The bottom line is that the router will phone home for all sorts of things, to multiple domains and there is nothing we can do about it. The data the router sends back to them is none of our business. If you are seriously concerned about privacy, Synology is not for you.
LIVING WITH THE ROUTER top
Every time I visit the Network Center app and click on Internet, there is an error message in red: "QuickConnect connection failed. Please check your network configurations." What is QuickConnect? And, why is it failing? The router is online just fine. On the QuickConnect tab, there is a checkbox to enable it that is NOT checked. So, why is it being invoked? This seems typical of the way Synology works. Features are on all the time, even if you never enabled them. We see this too in the open ports on the LAN side. I created a tech support ticket for this and the initial response was a few "probably" guesses.
The options for updating SRM are at Control Panel -> System -> Update and Restore tab -> Update Settings button. One of the options is a checkbox for "Check for SRM updates automatically. Even when it is off, the router nonetheless still checks for updates automatically.
When there is a new version of SRM, you are told this by a red dot on the icon for the control panel. Its like find the popes in the pizza. The notification should be a bit more obvious.
A glass half full story: SRM version 1.2.3-8017 Update 3 was released September 24, 2019 and then recalled on October 1st due to bugs. On the one hand, releasing software with multiple bugs is bad. On the other hand, Synology did own up to the problems and recalled the software. This is exactly why Peplink routers that can store two copies of the firmware are such a big deal to me. If a new firmware release has a bug, it is easy to reboot the router to the prior firmware. I never installed the buggy firmware, so I don't know exactly how Synology handled the fallback to the older software. I do know that I did not get an email, despite having registered the router and providing my email address as part of the registration.
There is an option to Enable HSTS at Control panel -> System -> SRM settings tab. The description says "Enabling HSTS forces browsers to use secured connections." It does not. As far as I could tell, this option did nothing. The option that did force HTTPS was just above it, called "Automatically redirect HTTP connections to HTTPS."
I did not connect the router directly to the Internet, instead I connected its WAN port to the LAN port of another router, one that was directly connected to the Internet. That meant that the Synology router thought its public IP address is 192.168.1.something. However, Synology also defaults to the 192.168.1.x subnet for its main/private network. The router correctly detected this problem and changed the subnet it uses for the main network to 10.0.4.x. Well done. The Guest Wi-Fi continued to use its default subnet of 192.168.2.x.
I have, so far, created three tech support tickets. When I went to create the fourth, the Synology support web site would not do so. Clicking the blue Next button did nothing but re-display the current page which had suggested KB articles related to my issue.
OUT OF THE BOX DEFAULTS top
Auto updating of the firmware is off
UPnP is on
WPS is on
IPv6 is (mostly) enabled
On the 2.4GHz band, it does not default to the standard channels (1, 6, 11)
Guest Wi-Fi devices are blocked from the main/private network and from each other
Denial of Service protection is off
If you create an OpenVPN connection without importing an .ovpn file, the VPN connection is ignored because the option to "Use default gateway on remote
network?" is disabled
All WAN side TCP ports are closed, except for two used for remote/external access (HTTP and HTTPS)
NOTE: There is no default for remote access, the user is asked to decide about this during the initial setup.
INTERESTING FEATURES top
The Synology RT2600ac has tons of features many of which I have not yet tried. Based on what I have seen so far, these are the most interesting features, both those that are available and those that are not. Keep in mind, I have no interest in Wi-Fi speed or range. Every other review can provide that information. FYI: the router is made in China.
AVAILABLE FEATURES
- You can install apps on the router. The only other router that I have seen that offers this is the Turris Omnia.
- To me, the sexiest feature is the optional, free RADIUS server from Synology. I have yet to try in on the router but have used the same software on a Synology NAS. Having a RADIUS server enables WPA2 Enterprise, a huge step up, security-wise, from the WPA2 Personal that everyone uses. In my opinion, this a more important upgrade than WPA3 which mostly about speed, not security.
- Despite the one minor issue I had, it stands head and shoulders above other routers in terms of self-updating.
- The router can be used without creating a Synology account. A couple features require an account, but they are optional. However, if you want to request technical support, that requires an account.
- It can be a VPN client out of the box and it supports multiple types of VPNs. If you install extra software (they call their apps "packages") then it can be a VPN server too. Again, multiple types of VPNs are supported. If you install the VPN server app (its called VPN Plus rather than VPN Server), then you can connect from away, into the router, and use RDP provided by the router to remotely control Windows machines on your LAN. Cool. I have not tried this, yet.
- You can schedule the router to reboot itself. Not just once, but on an ongoing basis. This can be handy to remove malware. Some router infections are removed when the router re-starts. So, restarting once a week in the middle of the night, might be a good thing.
- The Synology mesh system supports wired back haul.
- You can adjust the Wi-Fi radio transmit power.
- Some people like having lots of status lights on the top of the router, some do not. Better still, the router allows you to schedule when the status are enabled. If its too much light at night, schedule them to go dark at night and back on in the daytime. The cube shaped AmpliFi mesh router also does this.
- The router can handle two concurrent connections to the Internet. If they both use Ethernet, then one of the LAN ports is borrowed for the second ISP connection. Also supported is a 3G/4G dongle that plugs into a USB port on the router. Synology calls this Smart WAN. For multiple Internet connections, I would go with Peplink instead. It seems to be their specialty.
MISSING FEATURES
- Security by default, out of the box.
- Useful documentation. Everything Synology publishes is either marketing buzzwords or click-here-type this fill-in-the-blanks.
- There is no online demo of the SRM web interface.
- The RT2600ac can not do speed tests on its own. Google WiFi, AmpliFi and Eero offer this feature.
- The ability to log all activity from a device on the LAN. Say, for example, you read this Sept. 2019 ZDNet article Smart TVs send user data to tech heavyweights including Facebook, Google, Netflix and you wonder who or what your TV is communicating with. With a Synology router, you can't find out. Obviously with Peplink you can, that's how I logged the outbound connections made by the RT2600ac.
MAKING MESH top
When I am done kicking the tires on the RT2600ac, I will connect an MR2200ac to it, to extend the network. I suppose this is does not, technically, qualify as a mesh, but that's what everyone calls it. Based on what I have read beforehand, the procedure boils down to: power on the MR2200ac, wait for it to boot up, login to the RT2600ac, go to the Wi-Fi Connect app, click on Wi-Fi point and follow the instructions. What the instructions will be, Synology does not say.
Some things I will be look for: Can I tell, looking at the router or the mobile app, whether a client has connected to the router or to the extender? Which device does router.synology.com go to? Does the MR2200ac get its own IP address on both private and Guest subnet? Can I access the UI of the MR2200ac directly? Does it have different user accounts than the router? How does the installation of bug fixes work - are they always done in tandem? What is different about using Ethernet for backhaul?
Synology Wi-Fi Router MR2200acHardware Installation Guide No date. No mention of which SRM release it applies to.
Deploy your mesh Wi-Fi system with additional Wi-Fi points No date. No mention of which SRM release it applies to. Not very helpful, just says to follow the instructions in a wizard. Only discusses the web interface, not the mobile app.
Synology MR2200ac Review: A Fantastic Mesh Router by Dong Ngo Oct. 31, 2018. The article includes a warning: if, out of the box, a new MR2200ac is running SRM firmware earlier than version 1.2-7742 Update 1, then Synology recommends updating the firmware immediately and doing a hard reset.
In September 2019, I blogged about hidden Wi-Fi networks created by the router: Hidden Wi-Fi Networks on a Synology Router. While testing the router, I was only using the 2.4GHz Wi-Fi frequency band. Nonetheless, the router created a hidden Wi-Fi network on the 5GHz band. The lights on the router indicated that the 5GHz band was off, but, it was not. Simply put, the router was not doing what it was told. There is no excuse for this.
UPDATE December 21, 2022: Someone with a Synology RT6600AX router (SRM version 1.3-9193) ran across this blog while looking for information on the hidden network they found. This confirms that the issue still exists, which, to me, says a lot about Synology as a router vendor. Also, the hidden network that the router currently creates has WPS enabled even though WPS is disabled in the router web interface. And he tested something I did not - disabling the Wi-Fi at night on a set schedule. He found that while the RT6600AX does turn off the Wi-Fi on schedule, the hidden network remains.
FYI: the hidden network only replicates the 5GHZ-2 network, not the 2.4 and 5GHZ-1 networks.
SYNOLOGY RESOURCES top
What network ports are used by SRM services? by Synology. Undated. They don't believe in dates on their Knowledge Base articles.
The Users Guide for the RT2600ac. There is no last update date. As of September 2019, the manual is for SRM version 1.2, but is it 1.2.1 or 1.2.2 or 1.2.3?
The main online help page for SRM.
The Synology Router Forum.
The RT2600ac Release Notes page shows every update to SRM with a reasonable amount of detail. Synology, like Peplink, is not afraid to document the specific bugs that they fix.
At the download page for the RT2600ac you can download firmware, apps and documentation.
Synology brags about their security features Security in the IoT era. I am not impressed. More to come on this.
As of September 2019, the latest Synology router is the MR2200ac and it sells for about $140. The RT2600ac is the prior generation and it sells for around $200. The routers are very different. Synology published a comparison.
ZDNet article by David Gewirtz (February 19, 2019): Why I replaced Google Wifi with Synology's mesh networking gear (and why you might, too). In a difficult Wi-Fi environment, Google WiFi failed, Synology Wi-Fi succeeded.
You can install apps on the router. Synology calls apps "packages". Here are their Terms of Service for packages. In a similar vein, see the Synology Privacy Statement.
Building an intrusion prevention system for small businesses and homes. A Synology blog about the Safe Access and Threat Prevention packages in SRM 1.2. No author. No date.
UPDATES TO THIS PAGE top
UPDATE December 22, 2022: The Router News page has he results of the PWN2OWN contest that ran for four days in early December 2022. While many routers were hacked during the contest, Synology stood out for being hacked the most often.
UPDATE December 21, 2022: In the section above on Hidden Wi-Fi networks, there is an update about the current state of the Hidden Wi-Fi network that Synology creates.
UPDATE May 12, 2022: Synology just released a new router the RT6600ax. Or did they? The official website has an Availability page but its either buggy or empty on purpose. Like the RT2600ac it has every router feature ever invented. The latest features are only available on this new model with Synology saying they may get around to porting them to the older models sometime this year. The Ethernet ports are still plastic and still do not have LED lights. On the upside, it finally does VLANs.